Customers all around the globe are shifting from IP recognition to federated access for library authentication.
Federated authentication provides benefits to both admins and end users. For admins, it makes setting up a SAML single sign-on (SSO) connection to an E-Resource more scalable than setting up individual SAML SSO connections. For users, it provides a better, more personalized experience.
Let’s focus on the users. When we talk about a personalized user experience, we are talking about a personal folder, or bookshelf, that the user can login to aside from logging into the platform itself. For example, EBSCO's product offers a personalized MyEBSCO experience, which allows a user to save searches, full text and citations to folders and return to their research later on. In EBSCO's NewUI, the MyEBSCO dashboard is expanded to include organization of saved content into projects. Persistent folders are a common, basic value-add of personalization, though personal, unique authentication is also used to trigger more robust functionality such as ILS patron empowerment. There are many publishers that have similar features. Here is an example of a MyEBSCO folder:
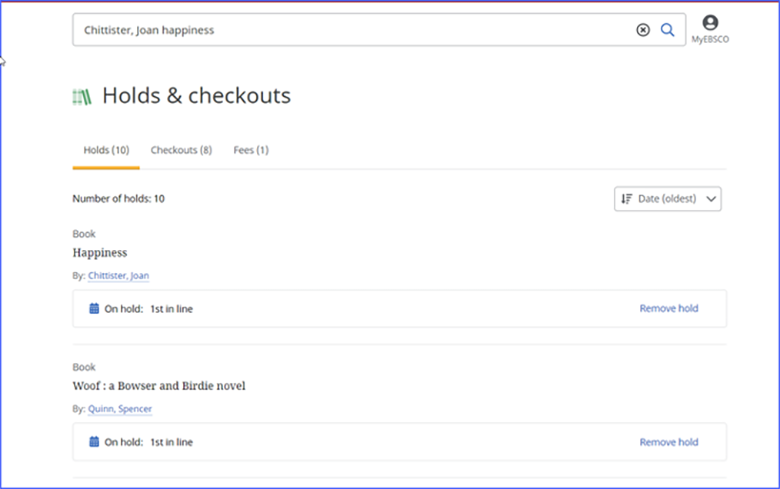
This is important - because the goal of a true seamless SSO experience is to eliminate as many hurdles as possible. For example, the login credentials a user needs to remember to access library resources and apps. Even if we have federated access set up to all your resources and users can jump between publisher websites without issue, they still may need to remember a handful of personal folder logins within each of these platforms. IP cannot solve this - by nature, this method is anonymous and therefore can get the user 'in the front door,' but cannot enable personalized functionality because we do not have the ability to key off the user's uniqueness. This is where federated access can help.
Federated access can in fact take care of both logins - institutional and personal. Many publishers can configure the experience, so the user is logged into the platform and their personal folder at the same time. This saves the user time and the need to remember more credentials.
How this happens from a technical perspective, is that we tell the publisher to look for a specific attribute, or data point that is sent through the SAML authentication. A really important takeaway is that we don't need to know the user's identity in order to provide them with personalized functionality - we just need to know their uniqueness.
SAML is an extremely secure protocol. Data is encrypted when sent across the web, so even if a nefarious actor was able to see an authentication, there wouldn’t be any data visible.
SAML is an extremely secure protocol. Data is encrypted when sent across the web, so even if a nefarious actor was able to see an authentication, there wouldn’t be any data visible.
What do we mean by that? An ID number is not something that an outside observer can typically use to know the user's identity. By definition, "pseudonymous" refers to an identifier that is opaque to an outside observer, e.g. no one at the vendor, or a malicious user seeking to breach credentials, could know the user's identity if they know the pseudonymous ID.
A really important takeaway is that we don't need to know the user's identity in order to provide them with personalized functionality - we just need to know their uniqueness.
A really important takeaway is that we don't need to know the user's identity in order to provide them with personalized functionality - we just need to know their uniqueness.
The most important quality of a pseudonymous ID is that it is unique to the user, and it is persistently the same each time the user signs into EBSCO.
If EBSCO sees a user with the persistent, unique ID of 12345ABCDE signing in from Imaginary University, then EBSCO can successfully return the user to their MyEBSCO folders and give access to the user’s saved research each time. However, knowing 12345ABCDE does not tell us the user's identity. If they see this attribute, then automatically log the user into their personal folder at the same time, and every time going forward. It’s a significant benefit to the user.
This feature of federated access is very powerful - but introduces the need to send data points or attributes to publishers so they can match the users with their folders. Naturally, this brings up the question of security - if we are sending data to a publisher, how can we make sure it’s safe and secure?
SAML is an extremely secure protocol. Data is encrypted when sent across the web, so even if a nefarious actor was able to see an authentication, there wouldn’t be any data visible.
Sometimes security of data transmission and storage is not enough. More and more, libraries and institutions focus on data minimization, wherein personal data is only shared when required for specific functionality. Federated access supports data minimization policies by allowing the library to control individual data points that are sent to specific vendors during authentication.
OpenAthens takes privacy preservation a step further by assigning a unique, pseudonymous identifier to each user that the library can optionally use for personalization. The identifier is unique to the user on a per-vendor basis, so as to preserve privacy across many research platforms.
The OpenAthens Federation is aware of these concerns and has built-in a solution to keep the benefits of personalization, without needing to send any user data by supporting the TargetedID attribute. TargetedID is a pseudonymous user identifier generated by OpenAthens and assigned to users - it has no connection to your local data whatsoever.
Instead of needing to send an email address or a name to a service provider to activate personalization, OpenAthens automatically assigns a TargetedID to every user behind the scenes. Example: ‘159qddg1761rh8d0uo48a2ko5q’
Each service sees a different value for the same account, but the value is consistent for the same service. The publisher gets the unique data point they need, and you as the customer do not need to share or release any of your information.
This is precisely why OpenAthens uses this attribute. The Targeted ID attribute is what can keep the user personalized and has no connection to the user data itself or across publishers. For some vendors, like EBSCO, the pseudonymous ID is the only data required to support personalized experiences, and no other personal data is required to achieve that functionality. Using OpenAthens, libraries can choose to release the pseudonymous ID and nothing else, and still reap the benefits of personalized SSO authentication, so subscribers and users get this benefit right off the bat. In the future, a new attribute called PairwiseID will replace TargetedID and accomplish the same goal.
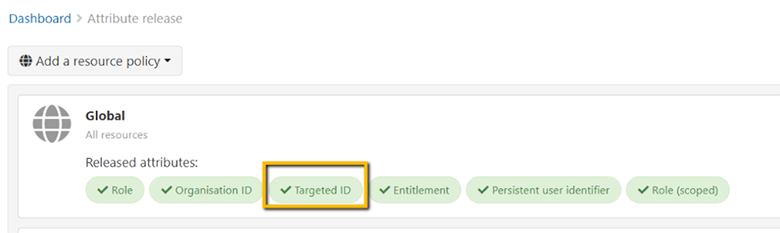
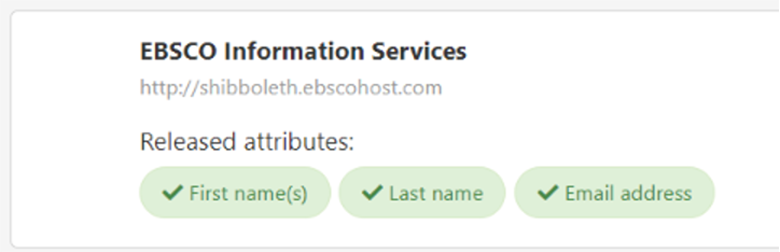
That being said, you may decide to release additional user attributes to certain e-content or library apps to further improve the personalized SSO experience for the user. OpenAthens Attribute Release tool gives you full control over your release policies, and only sends the attributes you want to the publisher of your choosing. For example, sharing first names with EBSCO via SSO logins is not required for access to the product and personalized functionality. hough if shared, it will greet the user by name in their MyEBSCO account, which is a value-add for some library patrons, and no other provider would receive this info:
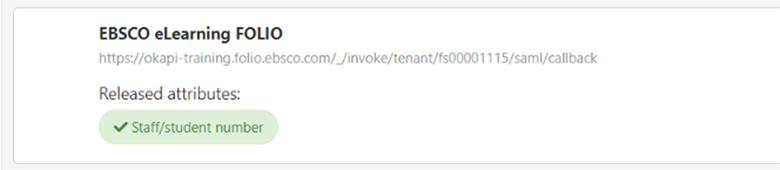
Maybe your ILS needs a student number to match the user's library status:
and your content management system (CMS) needs a department attribute to help route the user to certain sets of content:
This data translation is specific to the publisher or platform you choose to send it to.
When managing federations and SAML authentication, OpenAthens technology and user-friendly tools provide the best of both worlds - optimal user experience and easy ways for admins to control their data and comply with your institutional security policies. The TargetedID attribute can provide the baseline personalized user experience. An additional attribute release can be used as you see fit, and only where you see fit. With the inevitable shift away from IP address as the primary authentication, OpenAthens is the SaaS solution that will bring this balance to your library ecosystem.



